
At least seven Magecart groups are injecting TrojanOrders at approximately 38% of Magento and Adobe Commerce websites in November.
After a quiet summer, the number of attacks targeting the mail template vulnerability in Magento 2 and Adobe Commerce is rising fast. Merchants and developers should be on the lookout for TrojanOrders: orders that exploit a critical vulnerability in Magento stores. The trend in recent weeks paints a grim picture for ecommerce DevOps teams worldwide for the coming weeks.
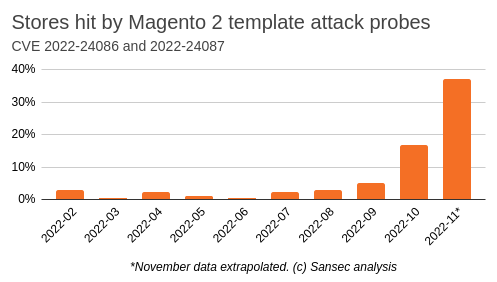
TrojanOrder attacks are surging
November is on track to see more Magento 2 template attack probes than the previous ten months combined. There is a big uptick in attacks using the mail template vulnerability in Magento 2 from February 2022 (CVE-2022-24086). Sansec estimates that at least a third of all Magento and Adobe Commerce stores have not been patched so far.
The attack consists of a few steps. A probe means “trying to trigger the system to send an email, with the exploit code in one of the fields.” An email is, among others, triggered by placing an order; that is why we call this attack TrojanOrder. Other triggers are “sign up as customer” or “share a wishlist.” A successful probe means the attacker can take over the website.
After gaining access to the website, the first order of business is installing a Remote Access Trojan, giving easy and permanent access to the website, often even after patching or upgrading the system. In the attacks we investigated, this backdoor is often, but not always, hidden in the file health_check.php, normally a legitimate Magento component.
Seven attack groups
Aggregating data from TrojanOrder incident cases at Sansec in the last weeks shows seven different attack vectors at the time of writing (November 2022). Seven attack vectors means at least seven Magecart groups now actively trying TrojanOrders on Magento 2 websites. Developing an attack route is difficult and expensive. Once a group has a working exploit (attack vector), they keep on using it unless it ceases to be effective.
There is a big increase of active scanning for the file that contains the backdoor (health_check.php). This is a sign of attacker groups are trying to take over infected sites from other groups.
What is behind this rise in attacks?
It is hard to pinpoint a single reason for the increase because the attack patterns are diffuse and successful attacks are mostly not detectable from the outside. But there are several reasons to contemplate.
Exploit kits for sale
A driving factor behind TrojanOrders is the availability of several low-cost exploit kits, easily acquired on hacking forums. This is an example from the popular exploit.in forum, but there are at least three others.
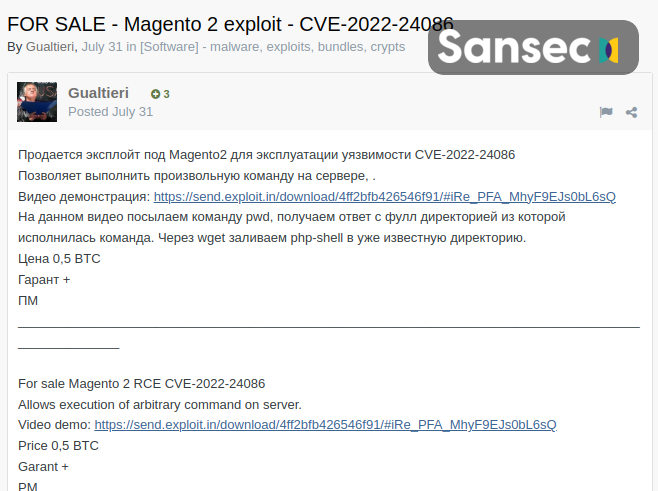
This particular exploit kit was basic but included an instruction video. Quickly, more advanced exploit kits were offered, some even claiming a 56% success rate.
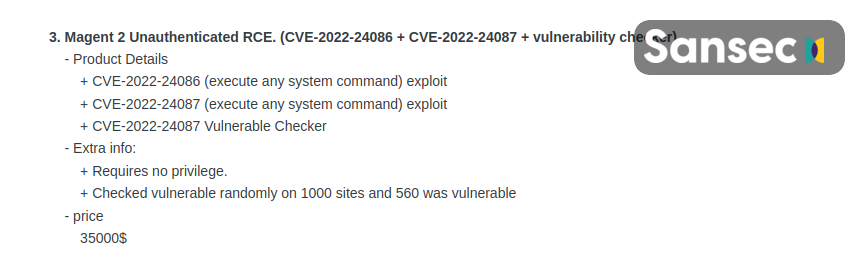
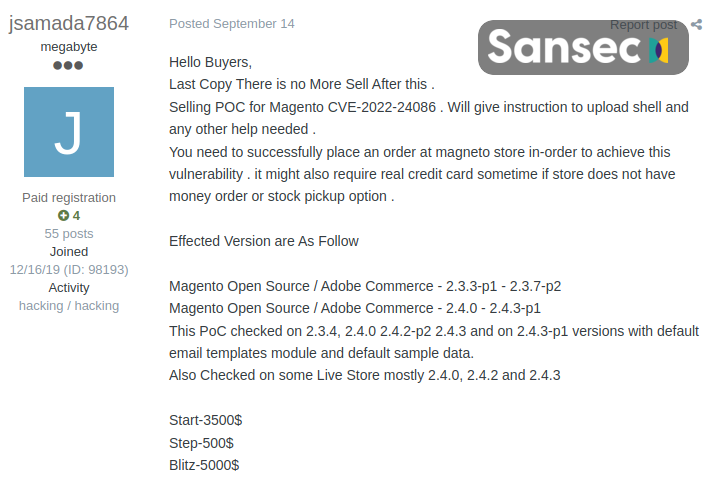
💡 How does this work? It is not always trivial to benefit from a vulnerability like CVE-2022-240486. Whenever such a vulnerability is published, attackers start with small-scale, interactive attacks. The goal is to achieve a repeatable process, also known as an exploit. Depending on the complexity of the vulnerability, this process can take hours or months. And when an exploit has finally been developed, it is either used for internal monetization or sold as a ready-to-use exploit kit to others.
The Magento exploits offered for sale were initially priced between $20k and $30k. However, as more exploit kits became available, the price has now dropped to 0.15 BTC, which means that it is now available to practically everyone.
Successful attacks lead to more attacks
If a group becomes more successful, the number of attacks will start to rise. Every extra website hacked brings in extra credit cards, extra payments, or extra private data.
It’s likely that it took a while for groups to find good attack vectors for this vulnerability. Now that the attack vectors have matured, the number of attacks is rising fast.
Perfect timing
November is the perfect attack month, ecommerce websites are (1) very busy with preparations for Black Friday and Cyber Monday and have a code freeze in place; (2) the number of orders is growing; and (3) the expected gains are bigger.
October, November, and December are, for most ecommerce websites, the most important months with regard to revenue. All focus is on sales and scaling, not on distractions such as patches and upgrades.
The more orders, the easier it is to overlook a TrojanOrder. Some merchants may get alerted by a strange order in their sales panel, but most staff will ignore it. November is the perfect month to execute this attack because of the high volume of transactions.
And, related, these months are also the best for harvesting customer and payment data from ecommerce websites. More transactions lead to more data. More transactions lead to slower detection, as card owners and issuers have more transactions to monitor.
You are patched, but are you secure?
Most Magento and Adobe Commerce websites were exposed to this vulnerability.
There is a chance you have already been attacked before applying one of the patches, and a backdoor was installed on your system. It is hard to estimate the probability of successful attacks because these backdoors are well-hidden on the server and can only be detected with a backend malware scanner like eComscan.
How can you see if you are being probed?
The first visible sign is a suspicious new customer record or transaction. Seeing customers pop up with names or addresses like “system” or “pwd”? Orders made by jarhovichbig@protonmail.com? Most likely, this is a TrojanOrder, and Sansec recommends inspecting your system as soon as possible.
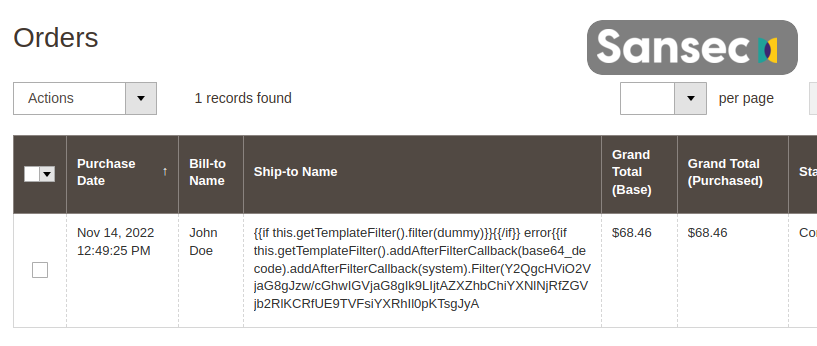
The best way to ensure your store is clean, is to use a backend malware scanner. Scan your store this month for free with eComscan using the coupon TROJANORDER.
The official Magento Security Scan can't find these TrojanOrders, because it is only scans from the outside (frontend malware scanner).
Emergency fix
We strongly recommend to upgrade to a support version of Magento or Adobe Commerce. If that is not immediately viable, you could consider implementing the following emergency patch to the top of app/bootstrap.php, which will block most attacks:
if(preg_match('/addafterfiltercallback/si', preg_replace("/[^A-Za-z]/", '', urldecode(file_get_contents("php://input"))))) {
header('HTTP/1.1 503 Service Temporarily Unavailable');
header('Status: 503 Service Temporarily Unavailable');
exit;
}
NB. This emergency patch comes without any warranty.
Read more
- If you want to know how to deconstruct an attack, you can visit our research article on Magento 2 template attacks. We detail three observed attack variations. Note: there are now at least seven variations.
- Security bulletin of Adobe.
- Contact Sansec or send us an email.
- Our original article on the CVE-2022-240086 vulnerability