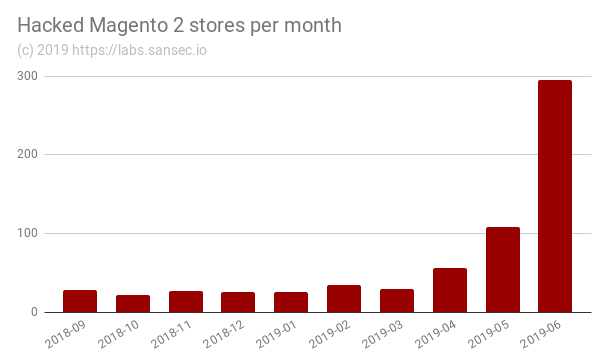
The number of hacked Magento 2 stores spiked in the last four weeks, after a critical security flaw was discovered in March and criminals stole admin passwords within 16 hours. Merchants are advised to implement emergency measures, even if they had already patched.
Update June 12th: While there was a surge in May, but we observed another 200% increase in the first two weeks of June. Graph updated.
First critical flaw for Magento 2
Magento 2 stores are often run by larger ($10-50M) and more professional organizations than its predecessor. So it is surprising that we observed a sharp increase in Magento 2 stores falling victim to credit card thieves recently.
However, in March the first critical bug in Magento 2 was published by security firm Ambionics. To the horror of many, the firm released sample exploit code just 2 days after Magento issued an emergency patch.
I feel it is not really professional to release a tool for exploiting it only 2 days after Magento release and on a Friday.
— Laurent Clouet (@laurent35240) March 30, 2019
While the provided exploit is only 80% functional, it wouldn't stop an experienced programmer from turning it into an effective attack method.
You got 16 hours to patch
The majority of merchants would implement emergency patch PRODSECBUG-2198 in the days after its release. But for many it would be too late: the first automated mass scanning of vulnerable sites was observed 16 hours after publication.
67.205.136.175 HTTP/1.1 "GET /catalog/product_frontend_action/synchronize?type_id=recently_products&ids[0][added_at]=&ids[0][product_id][from]=?&ids[0][product_id][to]=)))OR(SELECT+1+UNION+SELECT+2+FROM+DUAL+WHERE+1=1)--+- HTTP/1.1" 404 38347 133909
How the attack works
The observed attack consists of two stages. The first one is a "blind SQL injection" where attackers enumerate the admin_user table using a large number of requests (50 to 100K). This table contains the hashed (unreadable) passwords. However, with sufficient computing power, it is possible to reverse the hashes into the original passwords.
Magento 2 uses the SHA-256 hash algorithm, which is not recommended for storing passwords, because it is too fast. A consumer grade graphics card (such as the Nvidia GTX 1080 for $600) can compute 2.8 billion (!!) hashes per second (source). All possible 8-character passwords with just letters and numbers can be tried in 21 hours.
So after a few days, the attacker owns one or more admin passwords. Stage two of the attack is finding the actual Magento dashboard to login. Normally, Magento uses a random URL for the backend panel. However, yet another flaw in Magento exposes this hidden URL to anyone. This issue was reported on the Magento Github repository and then quickly removed by Adobe staff. But it is too late, criminals have been using this second flaw for weeks.
Then, with an admin password and access to the hidden dashboard, the attacker logs in, and adds a small snippet of malicious Javascript to the design/includes section of a store. We have observed malicious Javascript loaded from dozens of sites, such as:
https://bootstrapscdn.org/assets/
https://urbanin.com/wp-content/plugins/wp-migrate-db/asset/build/css/conversion_async.min.js
https://solarfm.com.co/wp-content/plugins/megapoll/templates/radio-table/checkout.min.js
https://soprr.ru/bitrix/components/bitrix/player/templates/.default/lang/ru/recaptcha.js
https://flycam.com.tr/wp-content/uploads/2015/01/jquery.min.js
https://zhilkom-24.ru/bitrix/cache/2018/gevents.min.js
The code behaves like a typical Magecart attack: it intercepts credit cards and PII from customers as they type them in. Attacker rejoices and sells the loot on the dark web for a profit of $5 to $30 per card.
Multiple attackers
The Ambionics exploit code was not completely functional and required some creativity to get it to work. Because we observed different implementations, we believe that at least 3 actors are actively searching for, and exploiting Magento 2 stores.
We believe that attackers focused on mass-retrieving passwords first, and are now slowly implementing skimmers on all of their "assets". So even if you have patched already, you may get infected once attackers reach your name on their list.
What a Magento 2 merchant can do
First, ensure that you are on par with all security patches.
Second, even if you already have patched: change all of your staffs admin passwords right away, as they were likely stolen before you patched. Use computer-generated passwords of at least 10 characters. This will significantly extend the time required to break the hashes. Here is a handy CLI command to change all passwords:
n98-magerun2 admin:user:list --format=csv | grep ,active | while read row;
do
user=$(echo $row | cut -d, -f2)
pass=$(tr -cd '[a-zA-Z0-9@#^*,/\;]' < /dev/urandom | fold -w10 | head -n1)
echo "$user -> $pass"
n98-magerun2 admin:user:change-password "$user" "$pass" >/dev/null
done
Third, inspect your site for malicious code or unauthorized access. Our eComscan forensic scanner can be valuable here (it was developed to aid in our own investigations).
Fourth, as long as Magento has not published a patch to hide the secret backend panel, you should implement extra protection. An IP restriction is recommended, use for example this plugin. If your staff uses dynamic IPs, it is recommended to have them use a VPN. This will not only guarantee a static IP but also enforce encryption.
Finally, install a malware & vulnerability monitor so you will be alerted immediately when something is amiss. Again, our eComscan scanner can run in monitoring mode and can even alert your dev team via Slack.
Got compromised? We are ready to help you to resolve this quickly.