Magecart definition
Magecart is a type of cybercrime where transaction data is intercepted during the checkout of an online store. Magecart attacks are also known as web skimming, digital skimming or formjacking.
In this article, you will read about the origin of Magecart, a list of famous attacks, a taxonomy of Magecart attack methods, and what you can do to prevent these attacks.
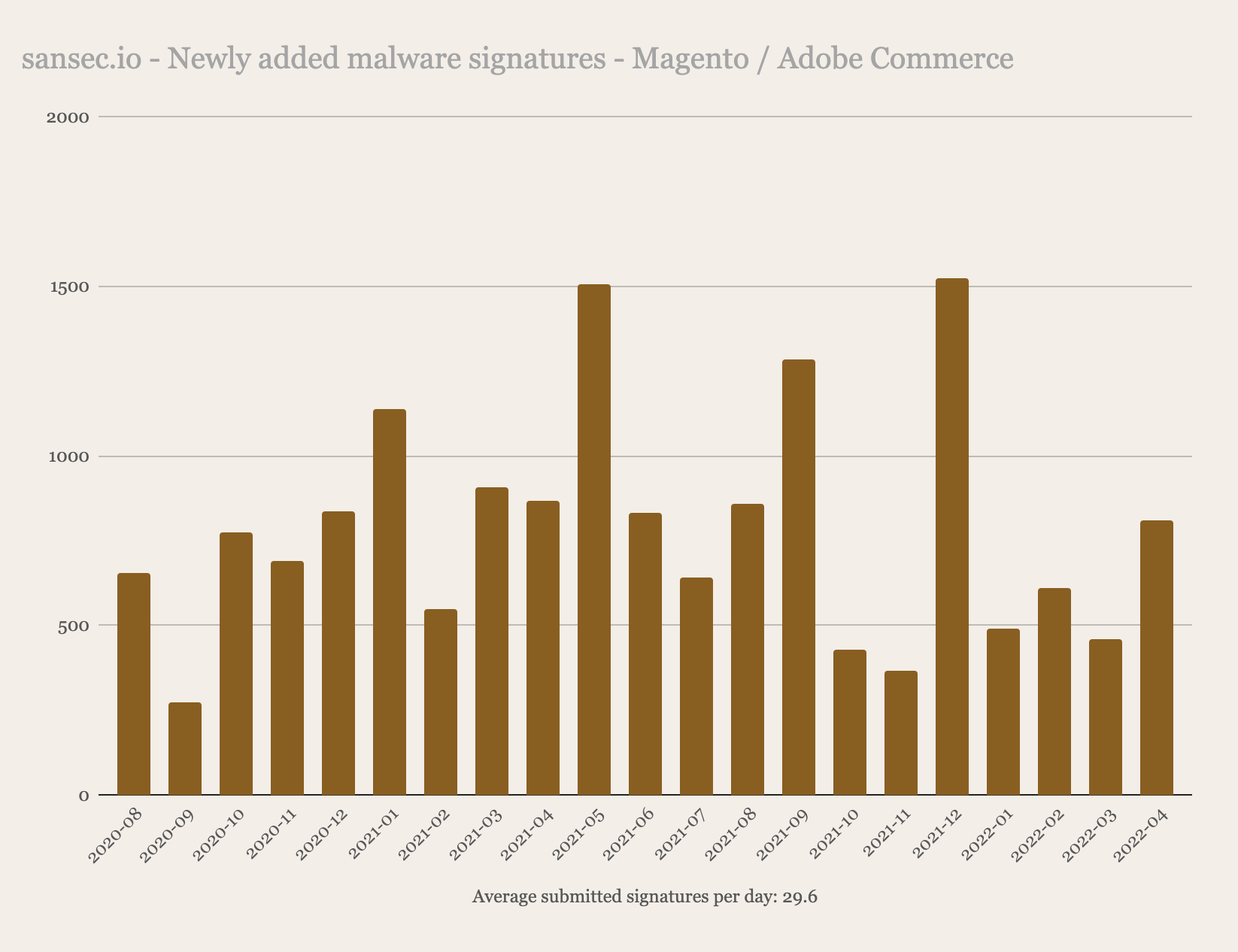
Magecart is still a very active threat to Magento, Adobe Commerce and other ecommerce platforms, Sansecs adds on average 30 malware signatures per day.
A quick intro to Magecart
Web skimming is just like physical skimming: your credit card details are stolen so that other people can spend your money. However, online skimming is more effective because a) it’s relatively easy and cheap to do, b) it’s harder to detect, and c) it is near impossible to trace the thieves.
In short, attackers (hackers) gain access to a store’s server and thus code using unpatched vulnerabilities in various popular e-commerce software. Once a store is under the control of a perpetrator, malware is installed (for instance a keylogger), that funnels live payment data to a collection server. This keylogger operates transparently, so customers and the merchant notice no apparent changes. Skimmed credit cards are then sold on the dark web for $5 to $30 each and subsequently used to steal money.
The name Magecart is a portmanteau of Magento and shopping cart. Magento dominated the ecommerce landscape from 2010 to 2020 when the whole criminal business of web skimming started. Magecart is now synonymous with web skimming and formjacking, “honoring” the name of its biggest victim. The concept is the same: skim customer and payment data out of forms on the ecommerce website to benefit the attacker.
Magecart history
The first Magecart-like attacks were observed as early as 2010. However, the first mass-executed Magecart attack, affecting thousands of stores, was reported in 2015 by Sansec.
Magento is a hugely popular open-source eCommerce platform that is used by hundreds of thousands of web stores around the world. After a serious vulnerability was discovered called Shoplift/SUPEE 5344, Magento became a big target for Magecart attacks in 2015. Sansec observed over 3,000 compromised Magento stores back in December 2015.
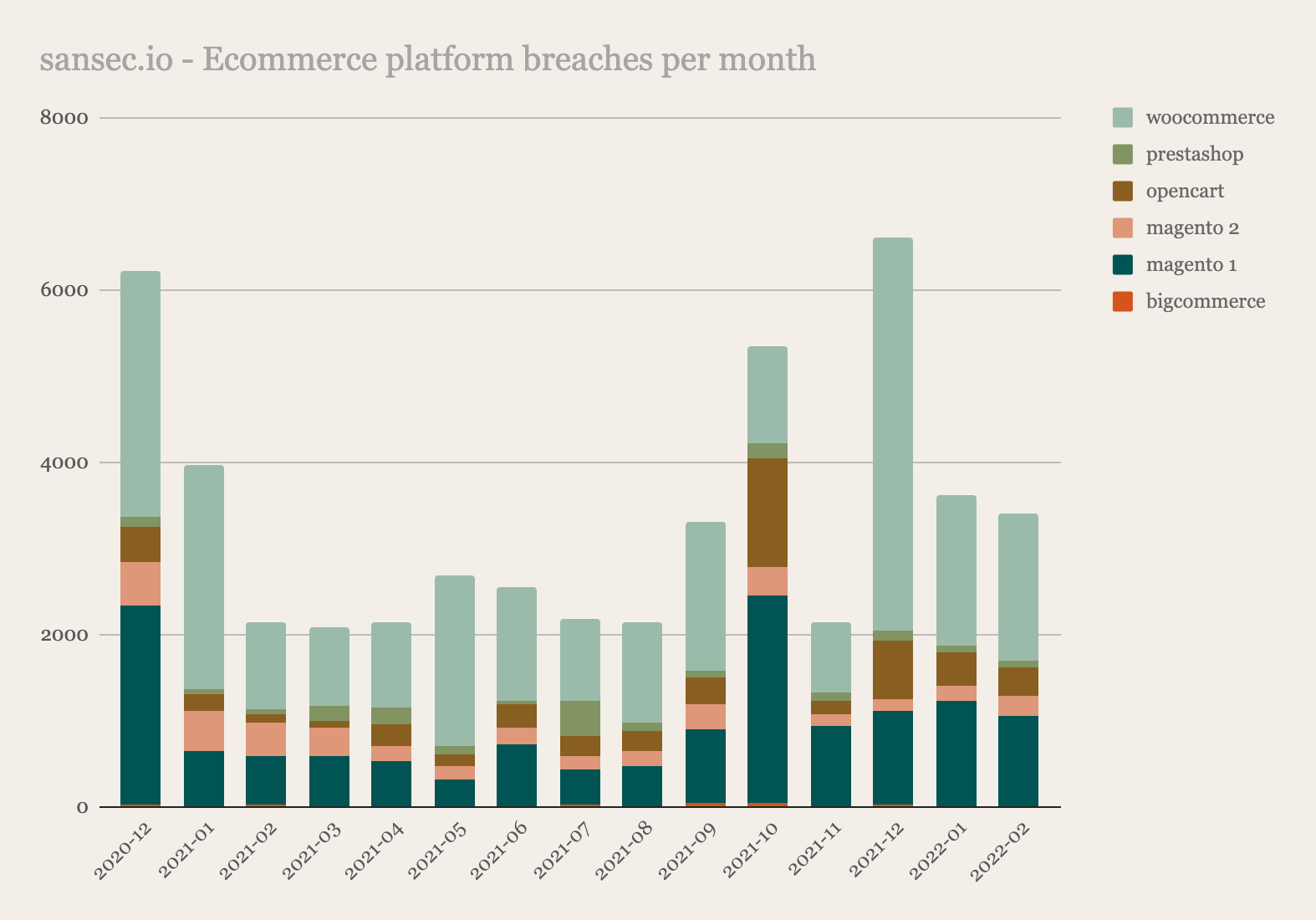
In the following years, this number of compromised stores quickly grew. As of 2022, Sansec has identified over 70,000 compromised stores that contained a digital skimmer at one point in time. More than 100,000 stores were affected if you include supply chain attack victims.
Web skimming is not limited to Magento, other open source ecommerce platforms are also targeted by cybercriminals. We track monthly breaches for the most used platforms.
Famous Magecart cases over the years
To date, Sansec identified over 70,000 ecommerce websites that suffered a Magecart attack. That is not surprising, since an incredible amount of e-commerce websites run on Magento.
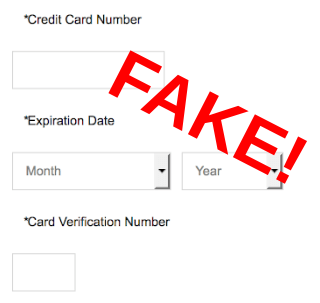
Closing the lid on a Tupperware container is easier than closing the code to Magecart attackers. In 2020 the payment form of the home products was bypassed and visitors were shown a lookalike (”fake payment form”).
The 2021 attack on “The Principality of Sealand” (an abandoned platform 10 kilometers of the coast of Great Britain in the North Sea, that claims independence) could be described as a successful attempt to stop people from buying a Duke or Baron title in a web store.
2022 saw another prominent hack: Segway, maker of the two-wheeled self-balancing personal transporters. Our global Early Breach Detection Network indicates a period of approximately 20 days before the door was finally closed.
An overview of well-known companies and organizations, affected by Magecart:
2015 Senate Republicans, LA Times 2016 ESET Security 2017 Red Cross 2018
Ticketmaster, British Airways, NewEgg 2019 Forbes, Macy’s, Procter and Gamble
2020 Intersport, Tupperware 2021 Sealand 2022 Segway, Element Vape
Magecart taxonomy
Sansec has collected samples of over 200 different Magecart malware families, and new ones are discovered every week. While merchants implement countermeasures, attackers come up with clever new methods. This overview illustrates a taxonomy of all known Magecart variants.
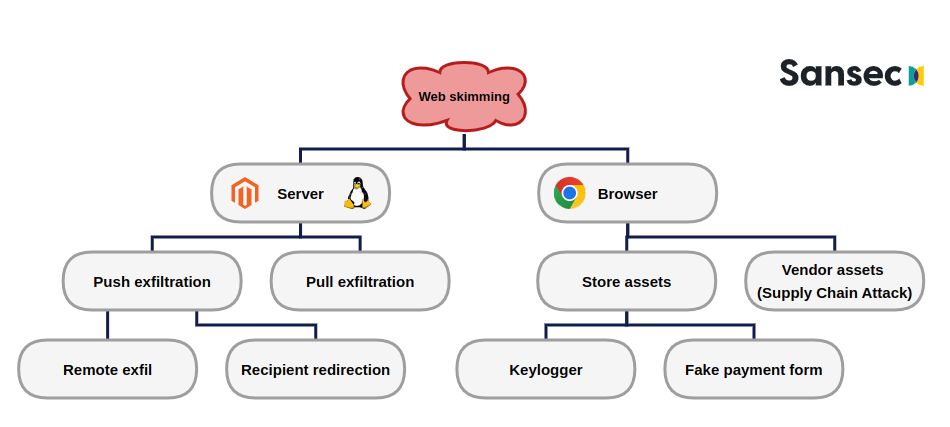
The most important distinction in various Magecart attack flavors is the location of the interceptor: browser (JavaScript) or server (usually PHP).
Front-end: Magecart in the browser
For browser Magecart, the malware is injected into the HTML or JavaScript source code. This source code either belongs directly to a store, or to an embedded third-party service. The latter is a special case called a Supply Chain Attack.
Browser Magecart malware typically attaches a keylogger to an existing payment form. However, the PCI council urges merchants to use external payment services. These external forms are harder to compromise. But… with server access is pretty easy for an attacker to inject a fake payment form into the checkout flow before the customer gets redirected to the external payment form. Once the customer completes the fake payment form, an error message is displayed, and the customer is redirected to the actual payment page.
A real of a fake payment form often looks exactly the same.
Most security software for ecommerce just observes this browser-side (front-end), it’s quite easy to set up: no server access or knowledge is needed, just enter an URL and you can crawl the ecommerce project.
Supply Chain Attack
The holy grail of Magecart client-side fraud is a Supply Chain Attack. Web stores normally depend on several third-party tools for marketing, analytics, visualization, cookie consent, etc. When an attacker hacks into such a service, s/he has effectively full control over all sites that use the service. With the press of a button, the attacker can inject its malware, which is now loaded on each and every store. And within seconds, all visitors of said web stores are running the skimming code.
While the potential damage of a Supply Chain Attack is huge, large-scale attacks have not materialized. In 2021, less than 1% of all Magecart incidents concerned a Supply Chain Attack.
Back-end: Magecart on the server
Many people think Magecart attacks are limited to these browser interceptions and many security vendors will tell this too. At Sansec we see that around 64% is backend or server-based (n=234, June 2022).
Since the first Magecart attacks in 2015, in the JavaScript on the customer- or client-side, attackers have gradually shifted to the backend. Probably different groups or individuals have specialized in different attack vectors.
In this type of attack, a piece of malware is injected during the checkout process and data is stolen, unknown to the merchant and visitor. This malware is hidden either in memory, the filesystem, or in the database. Sansec recently found malware posing as a legitimate Nginx process amongst its peers.
Once the malware is injected, all customer and payment data that is entered on the web store is copied to a well-hidden storage. The normal flow of the web store is not affected immediately, so payments proceed, orders are entered, payments are processed and products are delivered. A common method to exfiltrate private data is to encrypt and append it to a regular image on the server. The image is then periodically retrieved by the attacker.
After sufficient customer payment profiles are gathered, the data is exfiltrated at once instead of with every transaction, to minimize the risk of being caught (by a firewall, in the logs, etc). Sansec has worked on forensic cases where we saw several months’ worth of records stashed away for retrieval.
The only way to find this type of malware is with a specialized server-side security crawler, that has specific Magecart attack signatures.
Magecart attack stages
In general, there are 3 stages in a Magecart attack:
- Breach to gain access to the server.
- Inject the malware into the payment flow.
- Collect the desired data.
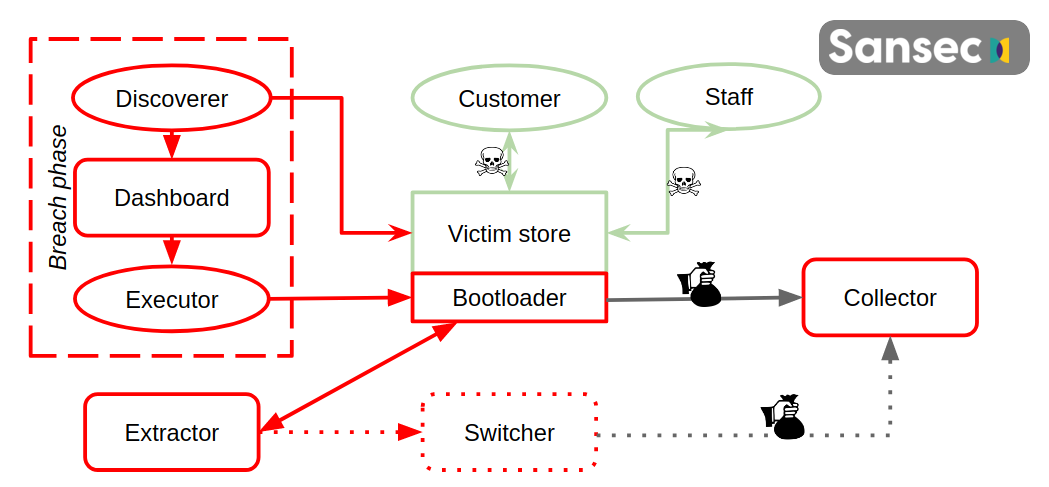
First, an attacker needs to gain access to the Magento web store source code
- a vulnerability in the ecommerce platform (Magento, Shopware);
- a vulnerability in an extension;
- a brute-forced or phished password;
- a configuration error. The second phase is the injection of the interception system (keylogger, server malware). Depending on the type of attack and the systems available to the attacker, malware is inserted somewhere in the order flow (before the external PSP, in the current flow the keystrokes are logged, etc).
Thirdly the customer and payment data is duplicated, using an interceptor and collector program. Private data is copied and is either (1) immediately sent to a collection server controlled by the attacker; or (2) hidden on the server and collected later, to minimize detection risk.
Attribution of Magecart attacks
Sansec estimates that the 70,000 observed attacks to date have been carried out by about 50 to 100 individuals. This figure is based on observed attack methods, malware infrastructure, and activity on underground forums.
But despite the popularity of this fraud, only a single arrest has been made so far. In 2020, Interpol and the Indonesian police arrested 3 individuals for Magecart hacks. Sansec was tracking this group for years and could link 571 hacked stores to them.
While there is not much evidence of the whereabouts of Magecart hackers, there are some indicators. The majority of Magecart hacking tools are advertised in the Russian language. And sometimes the skimming code contains words from a specific language. Sansec has discovered skimmers that contain Russian, English, Arabic, Chinese, Portuguese, and Indonesian phrases.
Finally, some Magecart attacks could be linked to nation-state hacking groups. Sansec showed that a North Korean-linked actor was responsible for skimming major American brands in 2020.
Effective Magecart prevention
With the knowledge of different Magecart style attacks, there are several things companies do to prevent a successful attack. The consequences of a successful breach can be incredibly costly:
-
Access to payment services is limited or blocked, so no payments can be received for several days or weeks.
-
Fines by PSP and privacy authorities.
-
Reputation damage that happens after a breach has been detected, communicating with press and customers about the company's security policies.
-
Loss of revenue if the ecommerce activities have to be stopped when a forensic and security team is working to gather evidence, find the entrance used, and perform emergency maintenance to patch things.
At Sansec we’ve worked on 100’s incidents and we’ve distilled a list of countermeasures to secure a Magento web store and minimize the risk:
- Restrict access to the Magento backend.
- In case of malware infection, change ALL admin & database passwords immediately.
- Activate 2FA and train your staff to deal with spearphishing. If an attacker can get in posing as an admin, it can be very hard to spot him/her.
- Use an (automated, hourly) malware monitor with Magecart-specific signatures.
- Perform an automated vulnerability audit on your ecommerce platform (Magento, Adobe Commerce) and used extensions on a regular basis, to be able to prevent an attacker from coming in.
And when dealing with an incident, a malware scanner must be used to find any backdoors the attackers may have installed.
Read more:
This page was last updated at Invalid DateTime